TTFA2: Email & Email Lists
Securing your email
What your can learn from this chapter;
- General tips for email privacy
- Some issues with mainstream email providers
- How to sign up for an activist email account and mailing lists
- How to encrypt your email
Where to sign up for an independent email
Because of the issues of spam, signing up for such an email is not usually an immediate and automated process. You can get an email at aktivix.org though a friend of a friend basis - if you know anyone with an aktivix.org email or in any of the following groups or networks, noborders, indymedia, hacktionlab, climate camp & social centre network - then send an email to aktivix-request@lists.aktivix.org letting them know the connection and the name of the email that you would like. It may be that the person of collective that you got this booklet from can help you to get an aktivix email account. You can also sign up for an account at Riseup.net and Autistic.org.
Where to sign up for an email list
Collectives that provide mailing lists include the following: aktivix.org, riseup.net, autistici.org. We recommend aktivix.org. Just send them an email about the list required to aktivix-request@lists.aktivix.org. Not all names are possible, so be prepared to change. It is nice if you can state your request simply in the subject line, such as: Subject: request for list for XYZ group/purpose, because it makes it easier to separate it from sp@m.
General tips
Email is great, it's decentralised and can be made very secure. Unfortunately, many people are moving away from it towards more insecure forms of communication.
Using BCC: When writing to a number of people use the BCC (blind carbon copy) field to send the email rather than To or CC fields. This ensures that no recipient knows who else has received the mail. Unless you have the permission of everyone on the your list to share their address with the other people, use BCC keep it secret. If you need the features of a mailing list, use one.
Issues with corporate email providers: There are two key issues with a commercial webmail provider (such as Google, Hotmail or Hushmail).
- They log usage and hand over your communications to the authorities on demand.
- They reserve the right to terminate your account as they see fit, effectively terminating a digital identity that you may have invested a lot of time in.
So when using email for your activism, consider choosing a provider you can trust, such as Riseup, Aktivix or Autistici.
Why use Independent Email?
Here we are referring to email run by collectives like riseup.net or aktivix.org. These services are run by media activist collectives who understand the need for privacy, anonymity and trust. You connect to them using a web page that runs over an encrypted connection. And unlike corporate providers, they will not give your emails over to the police without a warrant and a legal fight. If that happens, they will make it public if they can, so you (and the thousands of other activists on the same server) will know about it.
The secure email providers mentioned above also encrypt all messages sent between themselves, meaning that an email from an Aktivix user to a Riseup user is encrypted both as you compose it and when it travels between Aktivix and Riseup having been sent. Any Gmail (or similar) users on your mailing list are the weak link and you could recommend a more secure email account.
Why use Independent Email lists?
Some people simply maintain a list of contacts which you include in the to: or cc: field when you send an email. Or you can use a dedicated mailing list. These can handle large lists which you simply can’t do reliably manually. The mailing list server allows people to subscribe to or unsubscribe from the list and handles security and privacy much better, so members of the list don’t automatically know the email addresses of all the other members. The list server software can also create automatic archives which can be very useful.
Lists provided by activist tech collectives are only as good as their weakest point – in other words, if just one person on your mailing list has an “@googlemail.com” address, you can’t consider the list to be secure.
Consider the following points when creating lists:
- open or closed: can anyone subscribe or do subscriptions need to be approved?
- public or private: is the list to be advertised to the world, or is it run on a need to know basis?
- announce or discussion: is the list for receiving information only or for discussing something?
- moderated or not: are posts to the list to be moderated?
Securing your own email
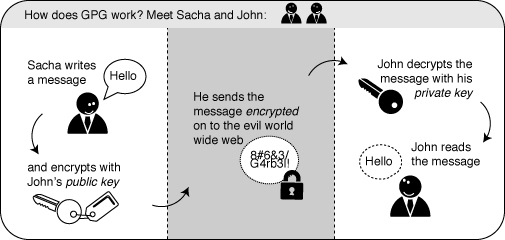
If you are concerned about privacy but not using a secure webmail service, or are communicating with someone who is not, or want an addition of level of personal security, you will want to encrypt your email. Encryption is the process of taking a plain text message and converting into something that looks like gobbledygook, which at the other end can be decrypted and the original message restored.
The Free Software tool of choice for this is called GPG, the GNU Privacy Guard.' Most people, even well rounded techies, find GPG tricky to get their heads around. Give yourself time to look at this - and it may take some time - but it is worth it.
GPG encryption uses pairs of numbers we refer to as key pairs. GPG will help you generate your key pair, comprised of a public key and a private one. You need to give your public key to anyone you wish to have encrypted communication with.
Your private key you will keep absolutely secret and never ever reveal to anyone ever, as it is used to decrypt email sent to you. It is so very secret that it needs protecting with a passphrase, which is basically a very long password.
GPG helps because by encrypting the email using the recipients' public keys, the sender can be assured that only the authorised recipients will be able to read it (privacy). If the email is signed by the sender's GPG key, the recipient can be assured of the identity of the sender (authenticity).
There are two main ways of using GPG. The first is with an email client like Thunderbird. The second is with an Add On for Firefox called FireGPG.
Enigmail and Thunderbird
Step by step instructions about setting up and using GPG with the popular Thunderbird email client can be found in the book Basic Internet Security.
Firefox and FireGPG
If you use webmail and it is not an option for you to use Thunderbird to check your mail, there is an add on which you can use to use GPG from within the Firefox web browser. In general it is best to use a mail program like Thunderbird in stead of using Webmail. Accessing your webmail from an untrusted environment like an Internet café is discouraged, because you cannot guarantee your password or traffic will not be intercepted. Using PGP in that situation may even make matters worse. Your secret key and passphrase, which you carry around on an USB-stick, may be read by a malicious program on the computer. In short, only use FireGPG to access your webmail in an environment you trust. There are instructions for installing FireGPG on their website. http://getfiregpg.org
What Next?
- Try to set up an email account with aktivix.org, riseup.net or similar
- Encourage your contacts to set up secure Email accounts
- Try out using GPG encryption